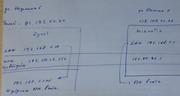
Помогите, если можете.
Схему и настройки микротика прилагаю.
Все досталось по наследству. Мое только сервер впн.
Из локальных сетей офисов все пингуеться.
Задача:
Подключиться к оф. Папина 213.109... по ВПН.
И потом подключиться по рдп к ПК 192.168.1.101 на оф. Неделина 5.
Что сделал на микротике.
Сервер РРРТ.
И два маршрута к lan 192.168.1.0/24.
vpn провайдера 172.20.46.0/24.
Что получилось.
Подключиться по впн к микротику.
Видно сеть на Папина 1 lan 192.168.1.0/24.
Мне нужно попасть на Неделина 5 на ПК 192.168.1.101.
# apr/03/2020 17:27:00 by RouterOS 6.45.1
# model = RouterBOARD 952Ui-5ac2nD
/interface bridge
add admin-mac=CE:2D:E0:3F:B0:DF arp=reply-only auto-mac=no fast-forward=no \
name=bridge-free-wifi
add admin-mac=CC:2D:E0:3F:B0:DF arp=proxy-arp auto-mac=no name=bridge-local
/interface ethernet
set [ find default-name=ether1 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full comment=WAN \
loop-protect=off loop-protect-disable-time=1m
set [ find default-name=ether2 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full
set [ find default-name=ether3 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full \
loop-protect-disable-time=1m
set [ find default-name=ether4 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full \
loop-protect-disable-time=1m
set [ find default-name=ether5 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full arp=proxy-arp \
comment="VPN from Nedelina 5" loop-protect=on
/interface pptp-server
add name=vnp_share user=ppp1_tck
/interface list
add name=WAN
add name=LAN
/ip hotspot profile
set [ find default=yes ] html-directory=flash/hotspot
/ip pool
add name=dhcp-pool-local ranges=192.168.1.2-192.168.1.150
add name=dhcp-pool-guest ranges=10.0.1.2-10.0.1.254
/ip dhcp-server
add add-arp=yes address-pool=dhcp-pool-local disabled=no interface=\
bridge-local lease-time=1d name=dhcp-local
add add-arp=yes address-pool=dhcp-pool-guest disabled=no interface=\
bridge-free-wifi name=dhcp-free-wifi
/queue simple
add burst-limit=10M/10M burst-threshold=10M/10M burst-time=10s/10s max-limit=\
3M/3M name=free-wifi target=bridge-free-wifi
/interface bridge port
add bridge=bridge-local interface=ether3
add bridge=bridge-local interface=ether4
add bridge=bridge-local interface=ether5
add bridge=bridge-local interface=wlan2
add bridge=bridge-local interface=wlan1
add bridge=bridge-free-wifi interface=guest-wlan1
add bridge=bridge-free-wifi interface=guest-wlan2
add bridge=bridge-local interface=ether2
add bridge=bridge-local interface=*D
/ip firewall connection tracking
set tcp-established-timeout=1h
/interface list member
add interface=ether1 list=WAN
add interface=bridge-local list=LAN
/interface pptp-server server
set enabled=yes
/ip address
add address=192.168.1.1/24 interface=bridge-local network=192.168.1.0
add address=213.109.xx.xx/20 interface=ether1 network=213.109.0.0
add address=10.0.1.1/24 interface=bridge-free-wifi network=10.0.1.0
add address=172.20.46.1/24 interface=ether2 network=172.20.46.0
/ip dhcp-server lease
add address=192.168.1.38 mac-address=10:7B:44:49:FE:25 server=dhcp-local \
use-src-mac=yes
add address=192.168.1.65 client-id=1:0:17:c8:37 9f mac-address=\
9f mac-address=\
00:17:C8:37:DE:9F server=dhcp-local
add address=192.168.1.67 client-id=1:40:4a:3:8:64:9a mac-address=\
40:4A:03:08:64:9A server=dhcp-local
/ip dhcp-server network
add address=10.0.1.0/24 dns-server=10.0.1.1,8.8.8.8 gateway=10.0.1.1
add address=192.168.1.0/24 dns-server=192.168.1.1,8.8.8.8 gateway=192.168.1.1 \
netmask=24
/ip dns
set allow-remote-requests=yes servers=8.8.8.8,109.195.0.5,5.3.3.3
/ip dns static
add address=127.0.0.1 comment=ADBlock name=lop.com
/ip firewall address-list
add address=109.172.47.21 list=TELEMIR
add address=213.59.158.74 list=DOMru
/ip firewall filter
add action=accept chain=input connection-nat-state="" connection-state=new \
connection-type="" protocol=gre
add action=accept chain=input dst-port=1723 protocol=tcp
add action=accept chain=input comment="Established \\ Related" \
connection-state=established,related
add action=accept chain=forward connection-state=established,related
add action=drop chain=input comment=Invalid connection-state=invalid \
in-interface=ether1
add action=drop chain=forward connection-state=invalid in-interface=ether1
add action=drop chain=input comment="Drop IN echo request" icmp-options=8:0 \
in-interface-list=WAN protocol=icmp src-address=!91.192.xx.xx \
src-address-list=!AllowIPRemoteManagement
add action=drop chain=input comment="Drop IN 443 port" dst-port=443 \
in-interface=ether1 log=yes protocol=tcp
add action=drop chain=input comment=Xaker_mazafaka dst-port=8291 protocol=tcp \
src-address-list=xaxakers
add action=accept chain=input comment="Allow Winbox" dst-port=8291 protocol=\
tcp
add action=jump chain=input comment="port knocking check" dst-address=\
213.109.xx.xx jump-target=portKnocking protocol=icmp
add action=add-src-to-address-list address-list=checkLevelOne \
address-list-timeout=10s chain=portKnocking comment=CheckLevelOne \
packet-size=128 protocol=icmp
add action=add-src-to-address-list address-list=checkLevelTwo \
address-list-timeout=10s chain=portKnocking comment=CheckLevelTwo \
packet-size=228 protocol=icmp src-address-list=checkLevelOne
add action=add-src-to-address-list address-list=TELEMIR address-list-timeout=\
1h chain=portKnocking comment=CheckLevelThree packet-size=328 protocol=\
icmp src-address-list=checkLevelTwo
add action=return chain=portKnocking
add action=add-src-to-address-list address-list="dns spoofing" \
address-list-timeout=1h chain=input comment=Anti_spoofing dst-port=53 \
in-interface=ether1 protocol=udp
add action=drop chain=input dst-port=53 in-interface=ether1 protocol=udp \
src-address-list="dns spoofing"
add action=accept chain=forward disabled=yes dst-address=192.168.1.0/24 \
src-address=1.1.1.2
/ip firewall nat
add action=src-nat chain=srcnat out-interface-list=WAN to-addresses=\
213.109.xx.xx
add action=dst-nat chain=dstnat dst-port=2060,3060,4001,966,2061 \
in-interface=ether1 protocol=tcp to-addresses=192.168.1.101 to-ports=2060
add action=dst-nat chain=dstnat dst-port=2060,3060,4001,966,2061 \
in-interface=ether1 protocol=udp to-addresses=192.168.1.101 to-ports=2060
add action=dst-nat chain=dstnat dst-port=5511-5513 in-interface=ether1 \
protocol=tcp to-addresses=192.168.1.101
add action=dst-nat chain=dstnat dst-port=5511-5513 in-interface=ether1 \
protocol=udp to-addresses=192.168.1.101
add action=dst-nat chain=dstnat dst-port=80 in-interface=ether1 log-prefix=\
CLARIS protocol=tcp to-addresses=192.168.1.38 to-ports=80
add action=dst-nat chain=dstnat disabled=yes port=3389 protocol=tcp \
src-address=1.1.1.2 to-addresses=192.168.1.101 to-ports=3389
/ip route
add distance=1 gateway=213.109.15.254
add distance=1 dst-address=172.20.46.0/24 gateway=vnp_share
add distance=1 dst-address=192.168.1.0/24 gateway=vnp_share
/ip route rule
add action=unreachable dst-address=192.168.1.0/24 src-address=10.0.1.0/24
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/ppp secret
add local-address=1.1.1.1 name=ppp1_tck remote-address=1.1.1.2
/system scheduler
add disabled=yes name=AutoADBlock on-event="/system script run AutoADBlock" \
policy=read,write,policy,test start-time=startup
# model = RouterBOARD 952Ui-5ac2nD
/interface bridge
add admin-mac=CE:2D:E0:3F:B0:DF arp=reply-only auto-mac=no fast-forward=no \
name=bridge-free-wifi
add admin-mac=CC:2D:E0:3F:B0:DF arp=proxy-arp auto-mac=no name=bridge-local
/interface ethernet
set [ find default-name=ether1 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full comment=WAN \
loop-protect=off loop-protect-disable-time=1m
set [ find default-name=ether2 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full
set [ find default-name=ether3 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full \
loop-protect-disable-time=1m
set [ find default-name=ether4 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full \
loop-protect-disable-time=1m
set [ find default-name=ether5 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full arp=proxy-arp \
comment="VPN from Nedelina 5" loop-protect=on
/interface pptp-server
add name=vnp_share user=ppp1_tck
/interface list
add name=WAN
add name=LAN
/ip hotspot profile
set [ find default=yes ] html-directory=flash/hotspot
/ip pool
add name=dhcp-pool-local ranges=192.168.1.2-192.168.1.150
add name=dhcp-pool-guest ranges=10.0.1.2-10.0.1.254
/ip dhcp-server
add add-arp=yes address-pool=dhcp-pool-local disabled=no interface=\
bridge-local lease-time=1d name=dhcp-local
add add-arp=yes address-pool=dhcp-pool-guest disabled=no interface=\
bridge-free-wifi name=dhcp-free-wifi
/queue simple
add burst-limit=10M/10M burst-threshold=10M/10M burst-time=10s/10s max-limit=\
3M/3M name=free-wifi target=bridge-free-wifi
/interface bridge port
add bridge=bridge-local interface=ether3
add bridge=bridge-local interface=ether4
add bridge=bridge-local interface=ether5
add bridge=bridge-local interface=wlan2
add bridge=bridge-local interface=wlan1
add bridge=bridge-free-wifi interface=guest-wlan1
add bridge=bridge-free-wifi interface=guest-wlan2
add bridge=bridge-local interface=ether2
add bridge=bridge-local interface=*D
/ip firewall connection tracking
set tcp-established-timeout=1h
/interface list member
add interface=ether1 list=WAN
add interface=bridge-local list=LAN
/interface pptp-server server
set enabled=yes
/ip address
add address=192.168.1.1/24 interface=bridge-local network=192.168.1.0
add address=213.109.xx.xx/20 interface=ether1 network=213.109.0.0
add address=10.0.1.1/24 interface=bridge-free-wifi network=10.0.1.0
add address=172.20.46.1/24 interface=ether2 network=172.20.46.0
/ip dhcp-server lease
add address=192.168.1.38 mac-address=10:7B:44:49:FE:25 server=dhcp-local \
use-src-mac=yes
add address=192.168.1.65 client-id=1:0:17:c8:37
00:17:C8:37:DE:9F server=dhcp-local
add address=192.168.1.67 client-id=1:40:4a:3:8:64:9a mac-address=\
40:4A:03:08:64:9A server=dhcp-local
/ip dhcp-server network
add address=10.0.1.0/24 dns-server=10.0.1.1,8.8.8.8 gateway=10.0.1.1
add address=192.168.1.0/24 dns-server=192.168.1.1,8.8.8.8 gateway=192.168.1.1 \
netmask=24
/ip dns
set allow-remote-requests=yes servers=8.8.8.8,109.195.0.5,5.3.3.3
/ip dns static
add address=127.0.0.1 comment=ADBlock name=lop.com
/ip firewall address-list
add address=109.172.47.21 list=TELEMIR
add address=213.59.158.74 list=DOMru
/ip firewall filter
add action=accept chain=input connection-nat-state="" connection-state=new \
connection-type="" protocol=gre
add action=accept chain=input dst-port=1723 protocol=tcp
add action=accept chain=input comment="Established \\ Related" \
connection-state=established,related
add action=accept chain=forward connection-state=established,related
add action=drop chain=input comment=Invalid connection-state=invalid \
in-interface=ether1
add action=drop chain=forward connection-state=invalid in-interface=ether1
add action=drop chain=input comment="Drop IN echo request" icmp-options=8:0 \
in-interface-list=WAN protocol=icmp src-address=!91.192.xx.xx \
src-address-list=!AllowIPRemoteManagement
add action=drop chain=input comment="Drop IN 443 port" dst-port=443 \
in-interface=ether1 log=yes protocol=tcp
add action=drop chain=input comment=Xaker_mazafaka dst-port=8291 protocol=tcp \
src-address-list=xaxakers
add action=accept chain=input comment="Allow Winbox" dst-port=8291 protocol=\
tcp
add action=jump chain=input comment="port knocking check" dst-address=\
213.109.xx.xx jump-target=portKnocking protocol=icmp
add action=add-src-to-address-list address-list=checkLevelOne \
address-list-timeout=10s chain=portKnocking comment=CheckLevelOne \
packet-size=128 protocol=icmp
add action=add-src-to-address-list address-list=checkLevelTwo \
address-list-timeout=10s chain=portKnocking comment=CheckLevelTwo \
packet-size=228 protocol=icmp src-address-list=checkLevelOne
add action=add-src-to-address-list address-list=TELEMIR address-list-timeout=\
1h chain=portKnocking comment=CheckLevelThree packet-size=328 protocol=\
icmp src-address-list=checkLevelTwo
add action=return chain=portKnocking
add action=add-src-to-address-list address-list="dns spoofing" \
address-list-timeout=1h chain=input comment=Anti_spoofing dst-port=53 \
in-interface=ether1 protocol=udp
add action=drop chain=input dst-port=53 in-interface=ether1 protocol=udp \
src-address-list="dns spoofing"
add action=accept chain=forward disabled=yes dst-address=192.168.1.0/24 \
src-address=1.1.1.2
/ip firewall nat
add action=src-nat chain=srcnat out-interface-list=WAN to-addresses=\
213.109.xx.xx
add action=dst-nat chain=dstnat dst-port=2060,3060,4001,966,2061 \
in-interface=ether1 protocol=tcp to-addresses=192.168.1.101 to-ports=2060
add action=dst-nat chain=dstnat dst-port=2060,3060,4001,966,2061 \
in-interface=ether1 protocol=udp to-addresses=192.168.1.101 to-ports=2060
add action=dst-nat chain=dstnat dst-port=5511-5513 in-interface=ether1 \
protocol=tcp to-addresses=192.168.1.101
add action=dst-nat chain=dstnat dst-port=5511-5513 in-interface=ether1 \
protocol=udp to-addresses=192.168.1.101
add action=dst-nat chain=dstnat dst-port=80 in-interface=ether1 log-prefix=\
CLARIS protocol=tcp to-addresses=192.168.1.38 to-ports=80
add action=dst-nat chain=dstnat disabled=yes port=3389 protocol=tcp \
src-address=1.1.1.2 to-addresses=192.168.1.101 to-ports=3389
/ip route
add distance=1 gateway=213.109.15.254
add distance=1 dst-address=172.20.46.0/24 gateway=vnp_share
add distance=1 dst-address=192.168.1.0/24 gateway=vnp_share
/ip route rule
add action=unreachable dst-address=192.168.1.0/24 src-address=10.0.1.0/24
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/ppp secret
add local-address=1.1.1.1 name=ppp1_tck remote-address=1.1.1.2
/system scheduler
add disabled=yes name=AutoADBlock on-event="/system script run AutoADBlock" \
policy=read,write,policy,test start-time=startup