С микрота пинг есть, а с компа нет
Добавлено: 02 янв 2022, 21:05
Привет, перенастраивал микрот и что-то пошло не так)
1ый микрот соединен со вторым по wireguard, также первый микрот соединен со вторым тоже по vpn.
Первый микрот 192.168.10.1
Второй микрот 192.168.11.1
ВПН подсеть между первым и вторым - 10.78.1.0
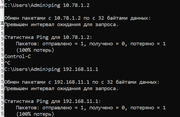
В общем проблема - с первого микрота пингуется второй микрот по адресам 192.168.11.1 и 10.78.1.2
Но с компа из лолкальной сети 192.168.10.0 адреса 192.168.11.1 и 10.78.1.2 не доступны, tracert с компа не уходит в подсеть 10.78.1.2, routes вроде сделаны, ранее все работало.
1ый микрот соединен со вторым по wireguard, также первый микрот соединен со вторым тоже по vpn.
Первый микрот 192.168.10.1
Второй микрот 192.168.11.1
ВПН подсеть между первым и вторым - 10.78.1.0
В общем проблема - с первого микрота пингуется второй микрот по адресам 192.168.11.1 и 10.78.1.2
Но с компа из лолкальной сети 192.168.10.0 адреса 192.168.11.1 и 10.78.1.2 не доступны, tracert с компа не уходит в подсеть 10.78.1.2, routes вроде сделаны, ранее все работало.
Код: Выделить всё
# jan/02/2022 20:56:12 by RouterOS 7.1.1
# software id = DBWY-B4HI
#
# model = RBD52G-5HacD2HnD
# serial number = BEEB0
/interface bridge
add admin-mac=C4:AD:34:80:4C:7F auto-mac=no name=bridge
/interface ethernet
set [ find default-name=ether1 ] name=WAN
/interface l2tp-server
add comment=ObitVpn name=l2tp-in1 user=vpnobituser
/interface wireless
set [ find default-name=wlan1 ] band=2ghz-b/g/n channel-width=20/40mhz-XX \
country=russia disabled=no distance=indoors frequency=auto installation=\
indoor mode=ap-bridge ssid=Mik2.4 wireless-protocol=802.11 wps-mode=\
disabled
set [ find default-name=wlan2 ] band=5ghz-a/n/ac channel-width=\
20/40/80mhz-XXXX country=russia disabled=no distance=indoors frequency=\
auto installation=indoor mode=ap-bridge ssid=Mik5 wireless-protocol=\
802.11 wps-mode=disabled
/interface l2tp-client
add allow=mschap2 comment=SkntVPN connect-to=188.2***.***.*** name=l2tp-out1 \
use-ipsec=yes user=MikrotikArt
/interface wireguard
add listen-port=13231 mtu=1420 name=WGMikrotik9kino
add listen-port=51821 mtu=1420 name=WgUbuntu
add disabled=yes listen-port=51820 mtu=1420 name=WgUbuntuReserv
/interface list
add name=LAN
add name=Internet
add name=VPN
/interface wireless security-profiles
set [ find default=yes ] authentication-types=wpa-psk,wpa2-psk eap-methods="" \
mode=dynamic-keys supplicant-identity=MikroTik
/ip ipsec policy group
add name=obitgroup
/ip ipsec profile
set [ find default=yes ] lifetime=8h
/ip ipsec proposal
set [ find default=yes ] enc-algorithms=\
aes-256-cbc,aes-256-ctr,aes-192-cbc,aes-128-cbc,aes-128-ctr,3des
/ip pool
add name=dhcp ranges=192.168.10.100-192.168.10.254
add name=vpnsrv ranges=192.168.50.50-192.168.50.150
add name=WG ranges=10.78.1.0/24
/ip dhcp-server
add address-pool=dhcp interface=bridge name=defconf
/ppp profile
add change-tcp-mss=yes dns-server=192.168.50.1 local-address=192.168.50.1 \
name=vpnsrv remote-address=vpnsrv
/routing ospf instance
add disabled=yes name=default-v2 router-id=10.78.1.1
/routing ospf area
# ospf instance not active
add instance=default-v2 name=backbone-v2
/routing table
add fib name=ToSknt
add fib name=ToRkn
add name=rtab-1
/user group
set full policy="local,telnet,ssh,ftp,reboot,read,write,policy,test,winbox,pas\
sword,web,sniff,sensitive,api,romon,dude,tikapp,rest-api"
/interface bridge port
add bridge=bridge interface=ether2
add bridge=bridge interface=ether3
add bridge=bridge interface=ether4
add bridge=bridge interface=ether5
add bridge=bridge interface=wlan1
add bridge=bridge interface=wlan2
/ip neighbor discovery-settings
set discover-interface-list=!Internet
/interface detect-internet
set detect-interface-list=all
/interface l2tp-server server
set authentication=mschap2 default-profile=vpnsrv enabled=yes use-ipsec=\
required
/interface list member
add interface=l2tp-out1 list=VPN
add interface=l2tp-in1 list=VPN
add interface=WGMikrotik9kino list=VPN
add interface=WAN list=Internet
add interface=WgUbuntu list=VPN
add interface=WgUbuntuReserv list=VPN
add interface=ether2 list=LAN
add interface=ether3 list=LAN
add interface=ether4 list=LAN
/interface wireguard peers
add allowed-address=224.0.0.5/32,0.0.0.0/0 endpoint-address=188.***.***.*** \
endpoint-port=13231 interface=WGMikrotik9kino public-key=\
"TRUgo**********************A+Qylgzh3GQs="
add allowed-address=0.0.0.0/0 disabled=yes endpoint-address=138.****.***.*** \
endpoint-port=51820 interface=WgUbuntuReserv public-key=\
"Ix3WiPA********************/G/J7n/6mM="
add allowed-address=0.0.0.0/0 endpoint-address=130.****.***.*** endpoint-port=\
51821 interface=WgUbuntu public-key=\
"Zjbj/A********************fovbvHO/f1I="
/ip address
add address=192.168.10.1/24 interface=bridge network=192.168.10.0
add address=95.***.***.***/27 interface=WAN network=95.***.***.0
add address=10.78.1.1/24 interface=WGMikrotik9kino network=10.78.1.0
add address=10.78.25.1/24 interface=WgUbuntuReserv network=10.78.25.0
add address=10.78.78.1/24 interface=WgUbuntu network=10.78.78.0
/ip dhcp-client
add disabled=yes interface=WAN
/ip dhcp-server network
add address=192.168.10.0/24 dns-server=192.168.10.1 gateway=192.168.10.1 \
netmask=24
/ip dns
set allow-remote-requests=yes use-doh-server=https://1.0.0.2/dns-query \
verify-doh-cert=yes
/ip firewall filter
add action=fasttrack-connection chain=forward connection-mark=!ipsec \
connection-state=established,related hw-offload=yes protocol=udp
add action=fasttrack-connection chain=forward connection-mark=!ipsec \
connection-state=established,related hw-offload=yes protocol=tcp
add action=accept chain=forward comment="Accept Forward established related" \
connection-state=established,related
add action=drop chain=forward comment="Drop invalid Forward" \
connection-state=invalid
add action=drop chain=forward comment="drop all packets for lan, no nat" \
connection-nat-state=!dstnat connection-state=new in-interface-list=\
Internet
add action=accept chain=input comment="Accept Input established related" \
connection-state=established,related
add action=drop chain=input comment="Drop Invalid Input" connection-state=\
invalid
add action=drop chain=input dst-port=53,5353,1253 in-interface-list=Internet \
protocol=udp
add action=drop chain=input dst-port=53,5353,1253 in-interface-list=Internet \
protocol=tcp
add action=jump chain=input comment="Protected - WinBox, ssh, telnet chain" \
connection-state=new dst-port=8291,22,23 in-interface-list=Internet \
jump-target=Protected protocol=tcp
add action=accept chain=forward comment="Accept forward dst-nat" \
connection-nat-state=dstnat
add action=accept chain=input comment=WireGuard dst-port=\
13231,51820,51821,51822 protocol=udp
add action=accept chain=input comment=L2TP connection-state="" dst-port=1701 \
protocol=udp
add action=accept chain=input comment=EoIP disabled=yes protocol=gre
add action=accept chain=input comment=OSPF protocol=ospf
add action=accept chain=input comment=IpSec protocol=ipsec-esp
add action=accept chain=input comment="IKE, IPsecNAT" connection-state="" \
dst-port=500,4500 protocol=udp
add action=accept chain=input comment=ICMP protocol=icmp
add action=accept chain=input comment="Winbox MAC" dst-port=20561 protocol=\
udp
add action=add-src-to-address-list address-list=BlackListProtected \
address-list-timeout=3d chain=Protected comment=\
"Protected - WinBox, ssh, telnet. Drop in RAW" connection-state="" \
src-address-list="ListProtected Stage 2"
add action=add-src-to-address-list address-list="ListProtected Stage 2" \
address-list-timeout=2m chain=Protected connection-state="" \
src-address-list="ListProtected Stage 1"
add action=add-src-to-address-list address-list="ListProtected Stage 1" \
address-list-timeout=1m chain=Protected connection-state=""
add action=accept chain=Protected
add action=drop chain=input comment="Drop All Other Input" in-interface-list=\
Internet
add action=drop chain=forward comment="Drop All Other Forward" \
in-interface-list=Internet
/ip firewall mangle
add action=mark-routing chain=prerouting comment="Mark To VPS Server Ubuntu" \
connection-state=new dst-address-list=Rkn new-routing-mark=ToRkn \
passthrough=no
add action=mark-routing chain=prerouting comment="Mark to SkyNet" \
connection-state=new dst-address-list=Sknt new-routing-mark=ToSknt \
passthrough=no
add action=mark-routing chain=prerouting comment=Main connection-state=new \
new-routing-mark=main passthrough=no src-address=192.168.10.0/24
add action=mark-connection chain=input comment="Mark IPSec" connection-state=\
new ipsec-policy=in,ipsec new-connection-mark=ipsec passthrough=no
add action=mark-connection chain=output comment="Mark IPSec" connection-mark=\
ipsec connection-state=new ipsec-policy=out,ipsec new-connection-mark=\
ipsec passthrough=no
add action=mark-connection chain=input comment="Mark OSPF" connection-state=\
new new-connection-mark=OSPF passthrough=no protocol=ospf
/ip firewall nat
add action=dst-nat chain=dstnat comment=IpCam disabled=yes dst-port=\
10554,1080,8091 in-interface-list=VPN protocol=tcp to-addresses=\
192.168.10.122
add action=dst-nat chain=dstnat comment=Dc++ dst-port=7113,9813 protocol=tcp \
to-addresses=192.168.10.195
add action=dst-nat chain=dstnat comment=Dc++ dst-port=28108,6250 protocol=udp \
to-addresses=192.168.10.195
add action=dst-nat chain=dstnat comment=uTorrent dst-port=15369 protocol=tcp \
to-addresses=192.168.10.195
add action=dst-nat chain=dstnat dst-port=15369 protocol=udp to-addresses=\
192.168.10.195
add action=passthrough chain=srcnat disabled=yes routing-mark=ToRkn
add action=passthrough chain=srcnat disabled=yes routing-mark=ToSknt
add action=redirect chain=dstnat dst-port=53,5353,1253 in-interface-list=VPN \
protocol=udp to-ports=53
add action=redirect chain=dstnat dst-port=53,5353,1253 in-interface-list=VPN \
protocol=tcp to-ports=53
add action=masquerade chain=srcnat out-interface-list=Internet
add action=masquerade chain=srcnat comment=\
"Allow acees to other subnets for ObitVpn" src-address=192.168.50.0/24
add action=masquerade chain=srcnat comment=\
"Allow acees to other subnets for WireGuardSknt" src-address=10.78.1.0/24
add action=masquerade chain=srcnat disabled=yes src-address=10.78.25.0/24
/ip firewall raw
add action=drop chain=prerouting in-interface-list=Internet src-address-list=\
BlackListProtected
/ip route
add comment=Obit disabled=no distance=1 dst-address=0.0.0.0/0 gateway=\
95.***.***.*** pref-src="" routing-table=main scope=30 \
suppress-hw-offload=no target-scope=10
add comment="SKNT WireGuard" disabled=no distance=1 dst-address=0.0.0.0/0 \
gateway=WGMikrotik9kino pref-src="" routing-table=ToSknt scope=30 \
suppress-hw-offload=no target-scope=10
add comment=SKNT disabled=no distance=1 dst-address=192.168.11.0/24 gateway=\
WGMikrotik9kino pref-src="" routing-table=main scope=30 \
suppress-hw-offload=no target-scope=10
add comment=UbuntuWireGuard disabled=no distance=1 dst-address=0.0.0.0/0 \
gateway=WgUbuntu pref-src="" routing-table=ToRkn scope=30 \
suppress-hw-offload=no target-scope=10
/ip service
set telnet address=192.168.0.0/16
set ftp disabled=yes
set www address=0.0.0.0/0 disabled=yes
set ssh address=192.168.0.0/16
set api disabled=yes
set winbox address=0.0.0.0/0
set api-ssl disabled=yes
/ip upnp
set enabled=yes
/ppp secret
add name=vpnobituser profile=vpnsrv service=l2tp
/routing ospf interface-template
# ospf area not active
add area=backbone-v2 auth=md5 auth-id=1 auth-key=Mikrotik interfaces=LAN \
networks=192.168.10.0/24
add area=backbone-v2 auth=md5 auth-id=1 auth-key=Mikrotik disabled=yes \
interfaces=WgUbuntuReserv networks=10.78.25.0/24
# ospf area not active
add area=backbone-v2 auth=md5 auth-id=1 auth-key=Mikrotik interfaces=\
WGMikrotik9kino networks=10.78.1.0/24
# ospf area not active
add area=backbone-v2 auth=md5 auth-id=1 auth-key=Mikrotik interfaces=WgUbuntu \
networks=10.78.78.0/24
/routing rule
add action=unreachable disabled=yes dst-address=192.168.11.0/24 interface=\
WGMikrotik9kino min-prefix=0 routing-mark=ToSknt
add action=lookup-only-in-table disabled=yes routing-mark=ToRkn table=ToRkn
add action=lookup-only-in-table disabled=yes routing-mark=ToSknt table=ToSknt
add action=lookup-only-in-table disabled=yes routing-mark=main table=main
/system clock
set time-zone-name=Europe/Moscow
/system identity
set name=MikroTik_Art
/system ntp client
set enabled=yes
/system ntp server
set enabled=yes manycast=yes
/system ntp client servers
add address=time.cloudflare.com
add address=time.windows.com
/system routerboard settings
set cpu-frequency=auto
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LAN