Я дошел до настройки связи двух MikroTik'ов через OpenVPN.
VPN канал поднимается и есть связь между шлюзами. А вот что касается связи между хостами, то ситуация до конца мне не понятна. Помогите, пожалуйста разобраться.
Вот схема:
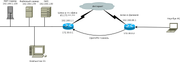
При подключении с ноутбука Ф1 на Сервер RDP (порт стандартный - 3389) все нормально, а вот подключение к сетевым папкам не работает, равно как и пинг на эти устройства.
С компьютера О1 работают и файловые ресурсы и пинг и, конечно, RDP.
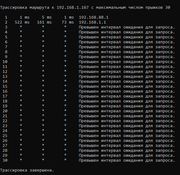
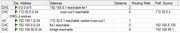
Маршруты Mikrotik в головном офисе:
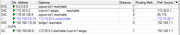
Маршруты Mikrotik в филиале:
Целиком конфиги. Головной офис:
Код: Выделить всё
# RouterOS 6.43.4
/interface pppoe-client
add add-default-route=yes disabled=no interface=ether1 name=pppoe-out1 \
password=* use-peer-dns=yes user=*
/interface sstp-server
add disabled=yes name=sstp-boris user=boris
/interface ovpn-server
add name="ovpn-in1 sergey" user=sergey
/ip pool
add name=OVPN_Pool ranges=172.30.0.1-172.30.0.253
/ppp profile
add local-address=172.30.0.1 name=OVPN_Connection remote-address=OVPN_Pool
/interface ovpn-server server
set certificate=server.crt_0 default-profile=OVPN_Connection enabled=yes \
port=65108 require-client-certificate=yes
/interface sstp-server server
set authentication=mschap2
/ip address
add address=192.168.1.1/24 interface=ether2 network=192.168.1.0
/ip dhcp-client
add dhcp-options=hostname,clientid interface=ether1
/ip dns
set allow-remote-requests=yes servers=8.8.8.8,77.88.8.1
/ip firewall address-list
add address=*** list="Port Scanners"
add address=*** comment=Ti list="RDP 1"
add address=*** comment=VI list="RDP 1"
add address=*** comment=Ca list="RDP 1"
add address=*** comment=Ei list="RDP 1"
add address=*** comment=va disabled=yes list="RDP 1"
add address=*** comment=de list="RDP 1"
add address=*** comment=Ki list="RDP 1"
/ip firewall filter
add action=accept chain=forward comment=\
"1.1. Forward and Input Established and Related connections" \
connection-state=established,related
add action=drop chain=forward connection-state=invalid
add action=accept chain=input connection-state=established,related
add action=drop chain=input connection-state=invalid
add action=add-src-to-address-list address-list=ddos-blacklist \
address-list-timeout=1d chain=input comment=\
"1.2. DDoS Protect - Connection Limit" connection-limit=100,32 \
in-interface-list=Internet protocol=tcp
add action=tarpit chain=input connection-limit=3,32 protocol=tcp \
src-address-list=ddos-blacklist
add action=jump chain=forward comment="1.3. DDoS Protect - SYN Flood" \
connection-state=new jump-target=SYN-Protect protocol=tcp tcp-flags=syn
add action=jump chain=input connection-state=new in-interface-list=Internet \
jump-target=SYN-Protect protocol=tcp tcp-flags=syn
add action=return chain=SYN-Protect connection-state=new limit=200,5:packet \
protocol=tcp tcp-flags=syn
add action=drop chain=SYN-Protect connection-state=new protocol=tcp \
tcp-flags=syn
add action=drop chain=input comment="1.4. Protected - Ports Scanners" \
src-address-list="Port Scanners"
add action=add-src-to-address-list address-list="Port Scanners" \
address-list-timeout=none-dynamic chain=input in-interface-list=Internet \
protocol=tcp psd=21,3s,3,1
add action=drop chain=input comment="1.5. Protected - WinBox Access" log=yes \
log-prefix="WINBOX DROP" src-address-list="Black List Winbox"
add action=add-src-to-address-list address-list="Black List Winbox" \
address-list-timeout=none-dynamic chain=input connection-state=new \
dst-port=8291 in-interface-list=Internet log=yes log-prefix=\
"BLACK WINBOX" protocol=tcp src-address-list="Winbox Stage 3"
add action=add-src-to-address-list address-list="Winbox Stage 3" \
address-list-timeout=1m chain=input connection-state=new dst-port=8291 \
in-interface-list=Internet protocol=tcp src-address-list="Winbox Stage 2"
add action=add-src-to-address-list address-list="Winbox Stage 2" \
address-list-timeout=1m chain=input connection-state=new dst-port=8291 \
in-interface-list=Internet protocol=tcp src-address-list="Winbox Stage 1"
add action=add-src-to-address-list address-list="Winbox Stage 1" \
address-list-timeout=1m chain=input connection-state=new dst-port=8291 \
in-interface-list=Internet protocol=tcp
add action=accept chain=input dst-port=8291 in-interface-list=Internet \
protocol=tcp
add action=accept chain=input comment="1.5.1 Allow OpenVPN" dst-port=65108 \
in-interface=pppoe-out1 log=yes protocol=tcp
add action=drop chain=input comment="1.6. Protected - OpenVPN Connections" \
log=yes log-prefix="OVPN BLACK" src-address-list="Black List OpenVPN"
add action=add-src-to-address-list address-list="Black List OpenVPN" \
address-list-timeout=none-dynamic chain=input connection-state=new \
dst-port=1194 in-interface-list=Internet log=yes log-prefix="BLACK OVPN" \
protocol=tcp src-address-list="OpenVPN Stage 3"
add action=add-src-to-address-list address-list="OpenVPN Stage 3" \
address-list-timeout=1m chain=input connection-state=new dst-port=1194 \
in-interface-list=Internet protocol=tcp src-address-list=\
"OpenVPN Stage 2"
add action=add-src-to-address-list address-list="OpenVPN Stage 2" \
address-list-timeout=1m chain=input connection-state=new dst-port=1194 \
in-interface-list=Internet protocol=tcp src-address-list=\
"OpenVPN Stage 1"
add action=add-src-to-address-list address-list="OpenVPN Stage 1" \
address-list-timeout=1m chain=input connection-state=new dst-port=1194 \
in-interface-list=Internet protocol=tcp
add action=accept chain=input dst-port=1194 in-interface-list=Internet \
protocol=tcp
add action=accept chain=input comment="1.8. Access Normal Ping" \
in-interface-list=Internet limit=50/5s,2:packet protocol=icmp
add action=drop chain=input comment="1.9. Drop All Other" in-interface-list=\
Internet
add action=accept chain=forward comment="RDP 1" dst-port=3389 \
in-interface=pppoe-out1 log-prefix="RDP 1" protocol=tcp \
src-address-list="RDP 1"
add action=drop chain=forward comment="RDP 2" dst-port=3389 in-interface=\
pppoe-out1 log=yes log-prefix="RDP 2" protocol=tcp
/ip firewall nat
add action=masquerade chain=srcnat out-interface=pppoe-out1
add action=netmap chain=dstnat disabled=yes dst-port=5037 in-interface=\
pppoe-out1 protocol=tcp to-addresses=192.168.1.111 to-ports=3389
add action=netmap chain=dstnat dst-port=1234 in-interface=pppoe-out1 \
protocol=tcp to-addresses=192.168.1.93 to-ports=1234
add action=netmap chain=dstnat dst-port=12345 in-interface=pppoe-out1 \
protocol=tcp to-addresses=192.168.1.93 to-ports=12345
add action=netmap chain=dstnat dst-port=1222 in-interface=pppoe-out1 \
protocol=tcp to-addresses=192.168.1.93 to-ports=1222
add action=netmap chain=dstnat dst-port=1223 in-interface=pppoe-out1 \
protocol=tcp to-addresses=192.168.1.93 to-ports=1223
add action=netmap chain=dstnat dst-port=1224 in-interface=pppoe-out1 \
protocol=tcp to-addresses=192.168.1.93 to-ports=1224
add action=netmap chain=dstnat dst-port=1225 in-interface=pppoe-out1 \
protocol=tcp to-addresses=192.168.1.93 to-ports=1225
add action=netmap chain=dstnat dst-port=1226 in-interface=pppoe-out1 \
protocol=tcp to-addresses=192.168.1.93 to-ports=1226
add action=netmap chain=dstnat dst-port=1227 in-interface=pppoe-out1 \
protocol=tcp to-addresses=192.168.1.93 to-ports=1227
add action=netmap chain=dstnat dst-port=1420 in-interface=pppoe-out1 \
protocol=tcp to-addresses=192.168.1.93 to-ports=1420
add action=netmap chain=dstnat dst-port=5036 in-interface=pppoe-out1 \
protocol=tcp to-addresses=192.168.1.95 to-ports=3389
add action=netmap chain=dstnat dst-port=5038 in-interface=pppoe-out1 \
protocol=tcp to-addresses=192.168.1.110 to-ports=3389
add action=netmap chain=dstnat dst-port=5039 in-interface=pppoe-out1 \
protocol=tcp to-addresses=192.168.1.109 to-ports=3389
add action=netmap chain=dstnat comment=\
"Port forward to red microtik for OVPN server" dst-port=64108 \
in-interface=pppoe-out1 log=yes protocol=tcp to-addresses=192.168.1.169 \
to-ports=64108
/ip route
add distance=1 dst-address=192.168.0.0/24 gateway=172.16.30.2 pref-src=\
172.16.30.1
add check-gateway=ping comment=OVPN distance=1 dst-address=192.168.88.0/24 \
gateway=172.30.0.2 pref-src=192.168.1.1
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/ppp secret
add local-address=172.16.30.1 name=* password=* \
remote-address=172.16.30.2 service=sstp
add name=sergey password=* profile=OVPN_Connection \
remote-address=172.30.0.2 service=ovpn
add name=OVPN_boris_home password=* profile=\
OVPN_Connection service=ovpn
Код: Выделить всё
# RouterOS 6.43.12
//ip pool
add name=dhcp ranges=192.168.88.10-192.168.88.254
/ip dhcp-server
add address-pool=dhcp disabled=no interface=bridge name=defconf
/ppp profile
add name=OVPN on-down="foreach i in [/ip route find where comment=\"OMG, it wo\
rkes\"] do={[/ip route remove \$i]}" on-up="/ip route add dst-address=192.\
168.1.0/24 gateway=172.30.0.1 distance=1 check-gateway=ping scope=255 comm\
ent=\"OMG, it workes\""
/interface ovpn-client
add certificate=client.crt_0 cipher=aes128 connect-to=85.175.*.* \
mac-address=02:E2:CA:78:*:* name=ovpn-out1 password=* \
port=65108 profile=OVPN user=sergey
/ip address
add address=192.168.88.1/24 interface=ether1 network=192.168.88.0
/ip dhcp-server network
add address=192.168.88.0/24 comment=defconf gateway=192.168.88.1
/ip dns
set allow-remote-requests=yes
/ip dns static
add address=192.168.88.1 name=router.lan
/ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
add action=masquerade chain=srcnat out-interface-list=WAN
/ip route
add check-gateway=ping comment="OMG, it workes" distance=1 dst-address=\
192.168.1.0/24 gateway=172.30.0.1 scope=255