У меня 2 роутера MikroTik: rb2011uias + hap lite.
rb2011uias - основной, в него приходит интернет и за ним компьютеры подключенные по LAN.
hap Lite - только для Wi-Fi.
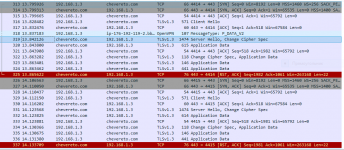
И вот проблема в том, что некоторые сайты не доступны. Если перейти на сайт, то получают вот такую ошибку - ERR_CONNECTION_RESET.
С телефона через моб Инет всё работает.
# apr/28/2020 17:31:04 by RouterOS 6.46.5
# software id = UJ3G-BKB9
#
# model = 2011UiAS
# serial number = *****************
/interface bridge
add admin-mac=00:0C:42:95:D4:6E auto-mac=no fast-forward=no name=bridge1
/interface ethernet
set [ find default-name=ether6 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full comment=\
FLEX-Internet mac-address=00:0C:42:95:D4:73 name=WAN
set [ find default-name=ether1 ] comment=MY-LAN disabled=yes mac-address=\
00:0C:42:95:D4:6E name=ether1-MASTER speed=100Mbps
set [ find default-name=ether2 ] disabled=yes mac-address=00:0C:42:95:D4:6F \
speed=100Mbps
set [ find default-name=ether3 ] mac-address=00:0C:42:95:D4:70 speed=100Mbps
set [ find default-name=ether4 ] disabled=yes mac-address=00:0C:42:95:D4:71 \
speed=100Mbps
set [ find default-name=ether5 ] disabled=yes mac-address=00:0C:42:95:D4:72 \
speed=100Mbps
set [ find default-name=ether7 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full comment=ASUS \
disabled=yes mac-address=00:0C:42:95:D4:74
set [ find default-name=ether8 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full comment=\
Proxmox mac-address=00:0C:42:95:D4:75
set [ find default-name=ether9 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full comment=Wi-Fi \
mac-address=00:0C:42:95:D4:76
set [ find default-name=ether10 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full disabled=yes \
mac-address=00:0C:42:95:D4:77
set [ find default-name=sfp1 ] disabled=yes mac-address=00:0C:42:95:D4:6D
/interface l2tp-client
add add-default-route=yes connect-to=***.255.255.*** disabled=no mrru=1600 \
name=l2tp-out1 password=***** user=*****
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip ipsec peer
add local-address=192.168.3.1 name=peer1 passive=yes
/ip ipsec policy group
add name=group1
/ip ipsec proposal
set [ find default=yes ] enc-algorithms=aes-256-cbc,aes-256-ctr,3des
/ip pool
add name=DHCP-users ranges=192.168.1.2-192.168.1.200
add name=vpn_l2tp ranges=192.168.3.2-192.168.3.10
/ip dhcp-server
add address-pool=DHCP-users authoritative=after-2sec-delay disabled=no \
interface=bridge1 lease-time=1d name=DHCP-server1
/ppp profile
add local-address=192.168.3.1 name=VPN-HOME remote-address=vpn_l2tp
/snmp community
set [ find default=yes ] addresses=0.0.0.0/0
/interface bridge port
add bridge=bridge1 hw=no interface=ether7
add bridge=bridge1 interface=ether1-MASTER
add bridge=bridge1 hw=no interface=ether8
add bridge=bridge1 hw=no interface=ether9
add bridge=bridge1 interface=ether2
add bridge=bridge1 hw=no interface=ether3
add bridge=bridge1 interface=ether4
add bridge=bridge1 interface=ether5
/ip neighbor discovery-settings
set discover-interface-list=none
/interface detect-internet
set detect-interface-list=all
/interface l2tp-server server
set authentication=mschap2 default-profile=default enabled=yes ipsec-secret=\
CbIIpSecPasswd one-session-per-host=yes use-ipsec=yes
/ip address
add address=***.***.***.***/24 interface=WAN network=***.***.***.***
add address=192.168.1.1/24 interface=ether1-MASTER network=192.168.1.0
/ip dhcp-server lease
add address=192.168.1.10 client-id=1:6c:3b:6b:cf:b4:49 mac-address=\
6C:3B:6B:CF:B4:49 server=DHCP-server1
add address=192.168.1.8 mac-address=EA:2B:85:F4:EF:AA server=DHCP-server1
add address=192.168.1.7 client-id=\
ff:ca:53:9:5a:0:2:0:0 11:80:71:4e:85:68:b9:9a:9b mac-address=\
11:80:71:4e:85:68:b9:9a:9b mac-address=\
9A:27:02:2C:07:75 server=DHCP-server1
/ip dhcp-server network
add address=192.168.1.0/24 dns-server=192.168.1.1,80.252.130.254 gateway=\
192.168.1.1 netmask=24
add address=192.168.3.0/24 gateway=192.168.3.1
/ip dns
set allow-remote-requests=yes cache-size=8096KiB servers=\
77.88.8.8,77.88.8.1
/ip firewall address-list
add address=0.0.0.0/8 list=BOGON
add address=10.0.0.0/8 list=BOGON
add address=100.64.0.0/10 list=BOGON
add address=127.0.0.0/8 list=BOGON
add address=169.254.0.0/16 list=BOGON
add address=172.16.0.0/12 list=BOGON
add address=192.0.0.0/24 list=BOGON
add address=192.0.2.0/24 list=BOGON
add address=192.168.0.0/16 list=BOGON
add address=198.18.0.0/15 list=BOGON
add address=198.51.100.0/24 list=BOGON
add address=203.0.113.0/24 list=BOGON
add address=224.0.0.0/4 list=BOGON
add address=77.88.8.1 list=dns_providers
add address=77.88.8.8 list=dns_providers
/ip firewall filter
add action=drop chain=input comment="dropping input port scanners" disabled=\
yes in-interface=l2tp-out1 log=yes log-prefix=drop-input_ \
src-address-list=black_addr
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="Port scanners to list " \
in-interface=l2tp-out1 protocol=tcp psd=21,3s,3,1
add action=accept chain=forward comment=\
"Accept forward established connections" connection-state=established \
out-interface=l2tp-out1
add action=accept chain=forward comment="Accept forward related connections" \
connection-state=related out-interface=l2tp-out1
add action=add-src-to-address-list address-list=black_addr \
address-list-timeout=2w1d chain=input comment="Add port scanners to list" \
dst-address-list=!dns_providers in-interface=l2tp-out1 protocol=tcp psd=\
21,3s,3,1
add action=tarpit chain=input comment="Suppress DoS attack" connection-limit=\
3,32 in-interface=l2tp-out1 protocol=tcp src-address-list=black_addr
add action=add-src-to-address-list address-list=black_addr \
address-list-timeout=1d chain=input comment="Detect DoS attack" \
connection-limit=10,32 in-interface=l2tp-out1 protocol=tcp
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="NMAP FIN Stealth scan" \
protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg
add action=accept chain=input comment=IP-TV disabled=yes log-prefix=IPTV-IN \
protocol=igmp
add action=accept chain=input disabled=yes dst-port=1234 log-prefix=IPTV-1234 \
protocol=udp
add action=accept chain=input comment="rule for L2TP_VPN" disabled=yes log=\
yes log-prefix=VPN1_ port=1701,500,4500 protocol=udp
add action=accept chain=input comment="rule for IPSEC for L2TP_VPN" disabled=\
yes protocol=ipsec-esp
add action=accept chain=forward comment=L2TP-LOCAL in-interface=!l2tp-out1 \
out-interface=bridge1 src-address=192.168.3.0/24
add action=drop chain=forward comment="Drop forward invalid connections" \
connection-state=invalid out-interface=l2tp-out1
add action=drop chain=input comment=\
"\C7\E0\EF\F0\E5\F2 \E4\EE\F1\F2\F3\EF\E0 \EA Mikrotik" dst-address=\
***.***.***.*** dst-port=8291 in-interface=l2tp-out1 log=yes log-prefix=\
TIK!_ protocol=tcp src-address-list=black_addr
add action=drop chain=input disabled=yes dst-port=80 protocol=tcp \
src-address=192.168.1.0/24
add action=drop chain=input comment="Drop other input FLEX" disabled=yes \
dst-address-list=!dns_providers in-interface=l2tp-out1 protocol=!udp
add action=drop chain=forward comment="DROP ALL !srcnat, dstnat" \
connection-nat-state=!srcnat,dstnat in-interface=l2tp-out1
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="SYN/FIN scan" protocol=tcp \
tcp-flags=fin,syn
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="SYN/FIN scan" protocol=tcp \
tcp-flags=fin,syn
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="SYN/RST scan" in-interface=\
l2tp-out1 protocol=tcp tcp-flags=syn,rst
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="SYN/RST scan" protocol=tcp \
tcp-flags=syn,rst
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="FIN/PSH/URG scan" \
in-interface=l2tp-out1 protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="ALL/ALL scan" in-interface=\
l2tp-out1 protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="NMAP NULL scan" protocol=tcp \
tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg
add action=drop chain=input comment="dropping port scanners" \
src-address-list="port scanners"
add action=add-src-to-address-list address-list=DNS_FLOOD \
address-list-timeout=none-dynamic chain=input comment="DNS FLOOD" \
disabled=yes dst-port=53 in-interface=l2tp-out1 protocol=udp
add action=drop chain=input comment="DNS FLOOD - DROP" disabled=yes dst-port=\
53 in-interface=l2tp-out1 protocol=udp
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="Port scanners to list " \
protocol=tcp psd=21,3s,3,1
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="FIN/PSH/URG scan" protocol=\
tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="ALL/ALL scan" protocol=tcp \
tcp-flags=fin,syn,rst,psh,ack,urg
/ip firewall nat
add action=masquerade chain=srcnat out-interface=l2tp-out1
add action=masquerade chain=srcnat disabled=yes src-address=192.168.88.0/24
add action=masquerade chain=srcnat comment="rule for Internet from L2TP_VPN" \
disabled=yes out-interface=*F00036 src-address=192.168.3.0/24
add action=dst-nat chain=dstnat comment="WEB - 250" disabled=yes dst-port=80 \
in-interface=l2tp-out1 protocol=tcp to-addresses=192.168.1.250 to-ports=\
80
add action=dst-nat chain=dstnat comment="WEB - 8" dst-port=80 in-interface=\
l2tp-out1 protocol=tcp to-addresses=192.168.1.8 to-ports=80
add action=dst-nat chain=dstnat comment=N****** dst-port=443 in-interface=\
l2tp-out1 log-prefix=NEXT_ protocol=tcp to-addresses=192.168.1.8 \
to-ports=443
add action=dst-nat chain=dstnat dst-port=465 in-interface=l2tp-out1 protocol=\
tcp to-addresses=192.168.1.7 to-ports=465
add action=dst-nat chain=dstnat dst-port=993 in-interface=l2tp-out1 protocol=\
tcp to-addresses=192.168.1.7 to-ports=993
add action=dst-nat chain=dstnat dst-port=25 in-interface=l2tp-out1 protocol=\
tcp to-addresses=192.168.1.7 to-ports=25
add action=dst-nat chain=dstnat comment=110 disabled=yes dst-port=110 \
in-interface=l2tp-out1 protocol=tcp to-addresses=192.168.1.7 to-ports=110
add action=dst-nat chain=dstnat dst-port=587 in-interface=l2tp-out1 protocol=\
tcp to-addresses=192.168.1.7 to-ports=587
add action=dst-nat chain=dstnat comment=ELASTIX disabled=yes dst-port=5001 \
in-interface=l2tp-out1 protocol=tcp to-addresses=192.168.2.35 to-ports=\
5001
add action=dst-nat chain=dstnat comment=OPEN-VPN disabled=yes dst-port=1194 \
in-interface=l2tp-out1 log-prefix=OVPN_ protocol=tcp to-addresses=\
192.168.1.84 to-ports=1194
add action=dst-nat chain=dstnat comment=TORRENT-WebUI dst-port=9091 \
in-interface=l2tp-out1 protocol=tcp to-addresses=192.168.1.8 to-ports=\
9091
add action=dst-nat chain=dstnat comment=Proxy dst-port=4128 in-interface=\
l2tp-out1 protocol=tcp to-addresses=192.168.1.53 to-ports=3128
add action=dst-nat chain=dstnat comment="\C4\EE\F1\F2\F3\EF \EA LAN 80" \
dst-address=***.***.***.*** dst-port=80 protocol=tcp src-address=\
192.168.1.0/24 to-addresses=192.168.1.8
add action=dst-nat chain=dstnat comment="\C4\EE\F1\F2\F3\EF \EA LAN 80 88/24" \
dst-address=***.***.***.*** dst-port=80 protocol=tcp src-address=\
192.168.88.0/24 to-addresses=192.168.1.8
add action=dst-nat chain=dstnat comment="\C4\EE\F1\F2\F3\EF \EA LAN 993" \
dst-address=***.***.***.*** dst-port=993 protocol=tcp src-address=\
192.168.1.0/24 to-addresses=192.168.1.7
add action=dst-nat chain=dstnat comment="\C4\EE\F1\F2\F3\EF \EA LAN-88 993" \
dst-address=***.***.***.*** dst-port=993 protocol=tcp src-address=\
192.168.88.0/24 to-addresses=192.168.1.7
add action=dst-nat chain=dstnat comment="\C4\EE\F1\F2\F3\EF \EA LAN 587" \
dst-address=***.***.***.*** dst-port=587 protocol=tcp src-address=\
192.168.1.0/24 to-addresses=192.168.1.7
add action=dst-nat chain=dstnat comment=\
"\C4\EE\F1\F2\F3\EF \EA LAN 587 - 88/24" dst-address=***.***.***.*** \
dst-port=587 protocol=tcp src-address=192.168.88.0/24 to-addresses=\
192.168.1.7
add action=dst-nat chain=dstnat comment="\C4\EE\F1\F2\F3\EF \EA LAN 443" \
dst-address=***.***.***.*** dst-port=443 protocol=tcp src-address=\
192.168.1.0/24 to-addresses=192.168.1.8 to-ports=443
add action=dst-nat chain=dstnat comment="\C4\EE\F1\F2\F3\EF \EA LAN 443-88" \
dst-address=***.***.***.*** dst-port=443 protocol=tcp src-address=\
192.168.88.0/24 to-addresses=192.168.1.8 to-ports=443
add action=masquerade chain=srcnat dst-address=192.168.1.8 dst-port=80 \
protocol=tcp src-address=192.168.1.0/24
add action=masquerade chain=srcnat comment=88 dst-address=192.168.1.8 \
dst-port=80 protocol=tcp src-address=192.168.88.0/24
add action=masquerade chain=srcnat comment="88 5001" dst-address=192.168.1.8 \
dst-port=5001 protocol=tcp src-address=192.168.88.0/24
add action=masquerade chain=srcnat comment="88 2869" dst-address=192.168.1.8 \
dst-port=2869 protocol=tcp src-address=192.168.88.0/24
add action=masquerade chain=srcnat comment="88 1900 " dst-address=192.168.1.8 \
dst-port=1900 protocol=udp src-address=192.168.88.0/24
add action=masquerade chain=srcnat dst-address=192.168.1.8 dst-port=443 \
protocol=tcp src-address=192.168.1.0/24
add action=masquerade chain=srcnat comment=88 dst-address=192.168.1.8 \
dst-port=443 protocol=tcp src-address=192.168.88.0/24
add action=masquerade chain=srcnat dst-address=192.168.1.7 dst-port=993 \
protocol=tcp src-address=192.168.1.0/24
add action=masquerade chain=srcnat dst-address=192.168.1.7 dst-port=587 \
protocol=tcp src-address=192.168.1.0/24
add action=masquerade chain=srcnat comment=88/24 dst-address=192.168.1.7 \
dst-port=587 protocol=tcp src-address=192.168.88.0/24
add action=masquerade chain=srcnat dst-address=192.168.1.7 dst-port=465 \
protocol=tcp src-address=192.168.1.0/24
add action=dst-nat chain=dstnat comment=DMZ disabled=yes in-interface=\
l2tp-out1 to-addresses=192.168.1.253
add action=dst-nat chain=dstnat comment="SIP -5060" dst-port=6060 \
in-interface=l2tp-out1 log-prefix=5060_ protocol=udp to-addresses=\
192.168.1.253 to-ports=5060
add action=dst-nat chain=dstnat comment="SIP -5061" dst-port=6061 \
in-interface=l2tp-out1 log-prefix=5061_ protocol=udp to-addresses=\
192.168.1.253 to-ports=5061
add action=dst-nat chain=dstnat comment="SIP -5160" dst-port=6160 \
in-interface=l2tp-out1 log-prefix=5160_ protocol=udp to-addresses=\
192.168.1.253 to-ports=5160
add action=dst-nat chain=dstnat comment="SIP -5160 - TEST" dst-port=5160 \
in-interface=l2tp-out1 log-prefix=5160_ protocol=udp to-addresses=\
192.168.1.253 to-ports=5160
add action=dst-nat chain=dstnat comment="SIP -5160 - LAN" dst-address=\
***.***.***.*** dst-port=5160 log-prefix=5160_ protocol=udp src-address=\
192.168.1.0/24 to-addresses=192.168.1.253 to-ports=5160
add action=dst-nat chain=dstnat comment="SIP -5160 - LAN-WIFI" dst-address=\
***.***.***.*** dst-port=5160 log-prefix=5160_ protocol=udp src-address=\
192.168.88.0/24 to-addresses=192.168.1.253 to-ports=5160
add action=dst-nat chain=dstnat comment="SIP -5161" dst-port=6161 \
in-interface=l2tp-out1 log-prefix=5161_ protocol=udp to-addresses=\
192.168.1.253 to-ports=5161
add action=dst-nat chain=dstnat comment="SIP -9000-10000" dst-port=\
10000-20000 in-interface=l2tp-out1 log-prefix=EEEE_ protocol=udp \
to-addresses=192.168.1.253 to-ports=10000-20000
add action=dst-nat chain=dstnat comment="RDP - .59" disabled=yes dst-port=\
17585 in-interface=l2tp-out1 protocol=tcp to-addresses=192.168.1.59 \
to-ports=3389
add action=dst-nat chain=dstnat comment=******* disabled=yes dst-port=****** \
in-interface=l2tp-out1 protocol=tcp to-addresses=192.168.1.150 to-ports=\
*****
/ip firewall service-port
set ftp disabled=yes
set tftp disabled=yes
set irc disabled=yes
set h323 disabled=yes
set sip disabled=yes ports=6060,6061
set pptp disabled=yes
set dccp disabled=yes
set sctp disabled=yes
/ip ipsec identity
add peer=peer1 remote-id=ignore secret=******
/ip route
add check-gateway=ping distance=2 gateway=***.***.***.***
add distance=1 dst-address=192.168.88.0/24 gateway=192.168.1.10
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set winbox address=192.168.1.0/24,192.168.3.0/24,192.168.88.0/24
set api-ssl disabled=yes
/ip ssh
set allow-none-crypto=yes forwarding-enabled=remote
/ip upnp
set enabled=yes
/ip upnp interfaces
add interface=bridge1 type=external
add interface=ether9 type=internal
/ppp secret
add name=vpn_ password=*************** profile=VPN-HOME service=l2tp
add name=honor_ password=*************** profile=VPN-HOME service=l2tp
add comment=******** local-address=192.168.3.13 name=********* \
password=***************** profile=VPN-HOME
/system clock
set time-zone-name=Europe/Moscow
/tool mac-server
set allowed-interface-list=none
/tool mac-server mac-winbox
set allowed-interface-list=none
/tool mac-server ping
set enabled=no
# software id = UJ3G-BKB9
#
# model = 2011UiAS
# serial number = *****************
/interface bridge
add admin-mac=00:0C:42:95:D4:6E auto-mac=no fast-forward=no name=bridge1
/interface ethernet
set [ find default-name=ether6 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full comment=\
FLEX-Internet mac-address=00:0C:42:95:D4:73 name=WAN
set [ find default-name=ether1 ] comment=MY-LAN disabled=yes mac-address=\
00:0C:42:95:D4:6E name=ether1-MASTER speed=100Mbps
set [ find default-name=ether2 ] disabled=yes mac-address=00:0C:42:95:D4:6F \
speed=100Mbps
set [ find default-name=ether3 ] mac-address=00:0C:42:95:D4:70 speed=100Mbps
set [ find default-name=ether4 ] disabled=yes mac-address=00:0C:42:95:D4:71 \
speed=100Mbps
set [ find default-name=ether5 ] disabled=yes mac-address=00:0C:42:95:D4:72 \
speed=100Mbps
set [ find default-name=ether7 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full comment=ASUS \
disabled=yes mac-address=00:0C:42:95:D4:74
set [ find default-name=ether8 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full comment=\
Proxmox mac-address=00:0C:42:95:D4:75
set [ find default-name=ether9 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full comment=Wi-Fi \
mac-address=00:0C:42:95:D4:76
set [ find default-name=ether10 ] advertise=\
10M-half,10M-full,100M-half,100M-full,1000M-half,1000M-full disabled=yes \
mac-address=00:0C:42:95:D4:77
set [ find default-name=sfp1 ] disabled=yes mac-address=00:0C:42:95:D4:6D
/interface l2tp-client
add add-default-route=yes connect-to=***.255.255.*** disabled=no mrru=1600 \
name=l2tp-out1 password=***** user=*****
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip ipsec peer
add local-address=192.168.3.1 name=peer1 passive=yes
/ip ipsec policy group
add name=group1
/ip ipsec proposal
set [ find default=yes ] enc-algorithms=aes-256-cbc,aes-256-ctr,3des
/ip pool
add name=DHCP-users ranges=192.168.1.2-192.168.1.200
add name=vpn_l2tp ranges=192.168.3.2-192.168.3.10
/ip dhcp-server
add address-pool=DHCP-users authoritative=after-2sec-delay disabled=no \
interface=bridge1 lease-time=1d name=DHCP-server1
/ppp profile
add local-address=192.168.3.1 name=VPN-HOME remote-address=vpn_l2tp
/snmp community
set [ find default=yes ] addresses=0.0.0.0/0
/interface bridge port
add bridge=bridge1 hw=no interface=ether7
add bridge=bridge1 interface=ether1-MASTER
add bridge=bridge1 hw=no interface=ether8
add bridge=bridge1 hw=no interface=ether9
add bridge=bridge1 interface=ether2
add bridge=bridge1 hw=no interface=ether3
add bridge=bridge1 interface=ether4
add bridge=bridge1 interface=ether5
/ip neighbor discovery-settings
set discover-interface-list=none
/interface detect-internet
set detect-interface-list=all
/interface l2tp-server server
set authentication=mschap2 default-profile=default enabled=yes ipsec-secret=\
CbIIpSecPasswd one-session-per-host=yes use-ipsec=yes
/ip address
add address=***.***.***.***/24 interface=WAN network=***.***.***.***
add address=192.168.1.1/24 interface=ether1-MASTER network=192.168.1.0
/ip dhcp-server lease
add address=192.168.1.10 client-id=1:6c:3b:6b:cf:b4:49 mac-address=\
6C:3B:6B:CF:B4:49 server=DHCP-server1
add address=192.168.1.8 mac-address=EA:2B:85:F4:EF:AA server=DHCP-server1
add address=192.168.1.7 client-id=\
ff:ca:53:9:5a:0:2:0:0
9A:27:02:2C:07:75 server=DHCP-server1
/ip dhcp-server network
add address=192.168.1.0/24 dns-server=192.168.1.1,80.252.130.254 gateway=\
192.168.1.1 netmask=24
add address=192.168.3.0/24 gateway=192.168.3.1
/ip dns
set allow-remote-requests=yes cache-size=8096KiB servers=\
77.88.8.8,77.88.8.1
/ip firewall address-list
add address=0.0.0.0/8 list=BOGON
add address=10.0.0.0/8 list=BOGON
add address=100.64.0.0/10 list=BOGON
add address=127.0.0.0/8 list=BOGON
add address=169.254.0.0/16 list=BOGON
add address=172.16.0.0/12 list=BOGON
add address=192.0.0.0/24 list=BOGON
add address=192.0.2.0/24 list=BOGON
add address=192.168.0.0/16 list=BOGON
add address=198.18.0.0/15 list=BOGON
add address=198.51.100.0/24 list=BOGON
add address=203.0.113.0/24 list=BOGON
add address=224.0.0.0/4 list=BOGON
add address=77.88.8.1 list=dns_providers
add address=77.88.8.8 list=dns_providers
/ip firewall filter
add action=drop chain=input comment="dropping input port scanners" disabled=\
yes in-interface=l2tp-out1 log=yes log-prefix=drop-input_ \
src-address-list=black_addr
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="Port scanners to list " \
in-interface=l2tp-out1 protocol=tcp psd=21,3s,3,1
add action=accept chain=forward comment=\
"Accept forward established connections" connection-state=established \
out-interface=l2tp-out1
add action=accept chain=forward comment="Accept forward related connections" \
connection-state=related out-interface=l2tp-out1
add action=add-src-to-address-list address-list=black_addr \
address-list-timeout=2w1d chain=input comment="Add port scanners to list" \
dst-address-list=!dns_providers in-interface=l2tp-out1 protocol=tcp psd=\
21,3s,3,1
add action=tarpit chain=input comment="Suppress DoS attack" connection-limit=\
3,32 in-interface=l2tp-out1 protocol=tcp src-address-list=black_addr
add action=add-src-to-address-list address-list=black_addr \
address-list-timeout=1d chain=input comment="Detect DoS attack" \
connection-limit=10,32 in-interface=l2tp-out1 protocol=tcp
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="NMAP FIN Stealth scan" \
protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg
add action=accept chain=input comment=IP-TV disabled=yes log-prefix=IPTV-IN \
protocol=igmp
add action=accept chain=input disabled=yes dst-port=1234 log-prefix=IPTV-1234 \
protocol=udp
add action=accept chain=input comment="rule for L2TP_VPN" disabled=yes log=\
yes log-prefix=VPN1_ port=1701,500,4500 protocol=udp
add action=accept chain=input comment="rule for IPSEC for L2TP_VPN" disabled=\
yes protocol=ipsec-esp
add action=accept chain=forward comment=L2TP-LOCAL in-interface=!l2tp-out1 \
out-interface=bridge1 src-address=192.168.3.0/24
add action=drop chain=forward comment="Drop forward invalid connections" \
connection-state=invalid out-interface=l2tp-out1
add action=drop chain=input comment=\
"\C7\E0\EF\F0\E5\F2 \E4\EE\F1\F2\F3\EF\E0 \EA Mikrotik" dst-address=\
***.***.***.*** dst-port=8291 in-interface=l2tp-out1 log=yes log-prefix=\
TIK!_ protocol=tcp src-address-list=black_addr
add action=drop chain=input disabled=yes dst-port=80 protocol=tcp \
src-address=192.168.1.0/24
add action=drop chain=input comment="Drop other input FLEX" disabled=yes \
dst-address-list=!dns_providers in-interface=l2tp-out1 protocol=!udp
add action=drop chain=forward comment="DROP ALL !srcnat, dstnat" \
connection-nat-state=!srcnat,dstnat in-interface=l2tp-out1
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="SYN/FIN scan" protocol=tcp \
tcp-flags=fin,syn
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="SYN/FIN scan" protocol=tcp \
tcp-flags=fin,syn
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="SYN/RST scan" in-interface=\
l2tp-out1 protocol=tcp tcp-flags=syn,rst
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="SYN/RST scan" protocol=tcp \
tcp-flags=syn,rst
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="FIN/PSH/URG scan" \
in-interface=l2tp-out1 protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="ALL/ALL scan" in-interface=\
l2tp-out1 protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="NMAP NULL scan" protocol=tcp \
tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg
add action=drop chain=input comment="dropping port scanners" \
src-address-list="port scanners"
add action=add-src-to-address-list address-list=DNS_FLOOD \
address-list-timeout=none-dynamic chain=input comment="DNS FLOOD" \
disabled=yes dst-port=53 in-interface=l2tp-out1 protocol=udp
add action=drop chain=input comment="DNS FLOOD - DROP" disabled=yes dst-port=\
53 in-interface=l2tp-out1 protocol=udp
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="Port scanners to list " \
protocol=tcp psd=21,3s,3,1
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="FIN/PSH/URG scan" protocol=\
tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack
add action=add-src-to-address-list address-list="port scanners" \
address-list-timeout=2w chain=input comment="ALL/ALL scan" protocol=tcp \
tcp-flags=fin,syn,rst,psh,ack,urg
/ip firewall nat
add action=masquerade chain=srcnat out-interface=l2tp-out1
add action=masquerade chain=srcnat disabled=yes src-address=192.168.88.0/24
add action=masquerade chain=srcnat comment="rule for Internet from L2TP_VPN" \
disabled=yes out-interface=*F00036 src-address=192.168.3.0/24
add action=dst-nat chain=dstnat comment="WEB - 250" disabled=yes dst-port=80 \
in-interface=l2tp-out1 protocol=tcp to-addresses=192.168.1.250 to-ports=\
80
add action=dst-nat chain=dstnat comment="WEB - 8" dst-port=80 in-interface=\
l2tp-out1 protocol=tcp to-addresses=192.168.1.8 to-ports=80
add action=dst-nat chain=dstnat comment=N****** dst-port=443 in-interface=\
l2tp-out1 log-prefix=NEXT_ protocol=tcp to-addresses=192.168.1.8 \
to-ports=443
add action=dst-nat chain=dstnat dst-port=465 in-interface=l2tp-out1 protocol=\
tcp to-addresses=192.168.1.7 to-ports=465
add action=dst-nat chain=dstnat dst-port=993 in-interface=l2tp-out1 protocol=\
tcp to-addresses=192.168.1.7 to-ports=993
add action=dst-nat chain=dstnat dst-port=25 in-interface=l2tp-out1 protocol=\
tcp to-addresses=192.168.1.7 to-ports=25
add action=dst-nat chain=dstnat comment=110 disabled=yes dst-port=110 \
in-interface=l2tp-out1 protocol=tcp to-addresses=192.168.1.7 to-ports=110
add action=dst-nat chain=dstnat dst-port=587 in-interface=l2tp-out1 protocol=\
tcp to-addresses=192.168.1.7 to-ports=587
add action=dst-nat chain=dstnat comment=ELASTIX disabled=yes dst-port=5001 \
in-interface=l2tp-out1 protocol=tcp to-addresses=192.168.2.35 to-ports=\
5001
add action=dst-nat chain=dstnat comment=OPEN-VPN disabled=yes dst-port=1194 \
in-interface=l2tp-out1 log-prefix=OVPN_ protocol=tcp to-addresses=\
192.168.1.84 to-ports=1194
add action=dst-nat chain=dstnat comment=TORRENT-WebUI dst-port=9091 \
in-interface=l2tp-out1 protocol=tcp to-addresses=192.168.1.8 to-ports=\
9091
add action=dst-nat chain=dstnat comment=Proxy dst-port=4128 in-interface=\
l2tp-out1 protocol=tcp to-addresses=192.168.1.53 to-ports=3128
add action=dst-nat chain=dstnat comment="\C4\EE\F1\F2\F3\EF \EA LAN 80" \
dst-address=***.***.***.*** dst-port=80 protocol=tcp src-address=\
192.168.1.0/24 to-addresses=192.168.1.8
add action=dst-nat chain=dstnat comment="\C4\EE\F1\F2\F3\EF \EA LAN 80 88/24" \
dst-address=***.***.***.*** dst-port=80 protocol=tcp src-address=\
192.168.88.0/24 to-addresses=192.168.1.8
add action=dst-nat chain=dstnat comment="\C4\EE\F1\F2\F3\EF \EA LAN 993" \
dst-address=***.***.***.*** dst-port=993 protocol=tcp src-address=\
192.168.1.0/24 to-addresses=192.168.1.7
add action=dst-nat chain=dstnat comment="\C4\EE\F1\F2\F3\EF \EA LAN-88 993" \
dst-address=***.***.***.*** dst-port=993 protocol=tcp src-address=\
192.168.88.0/24 to-addresses=192.168.1.7
add action=dst-nat chain=dstnat comment="\C4\EE\F1\F2\F3\EF \EA LAN 587" \
dst-address=***.***.***.*** dst-port=587 protocol=tcp src-address=\
192.168.1.0/24 to-addresses=192.168.1.7
add action=dst-nat chain=dstnat comment=\
"\C4\EE\F1\F2\F3\EF \EA LAN 587 - 88/24" dst-address=***.***.***.*** \
dst-port=587 protocol=tcp src-address=192.168.88.0/24 to-addresses=\
192.168.1.7
add action=dst-nat chain=dstnat comment="\C4\EE\F1\F2\F3\EF \EA LAN 443" \
dst-address=***.***.***.*** dst-port=443 protocol=tcp src-address=\
192.168.1.0/24 to-addresses=192.168.1.8 to-ports=443
add action=dst-nat chain=dstnat comment="\C4\EE\F1\F2\F3\EF \EA LAN 443-88" \
dst-address=***.***.***.*** dst-port=443 protocol=tcp src-address=\
192.168.88.0/24 to-addresses=192.168.1.8 to-ports=443
add action=masquerade chain=srcnat dst-address=192.168.1.8 dst-port=80 \
protocol=tcp src-address=192.168.1.0/24
add action=masquerade chain=srcnat comment=88 dst-address=192.168.1.8 \
dst-port=80 protocol=tcp src-address=192.168.88.0/24
add action=masquerade chain=srcnat comment="88 5001" dst-address=192.168.1.8 \
dst-port=5001 protocol=tcp src-address=192.168.88.0/24
add action=masquerade chain=srcnat comment="88 2869" dst-address=192.168.1.8 \
dst-port=2869 protocol=tcp src-address=192.168.88.0/24
add action=masquerade chain=srcnat comment="88 1900 " dst-address=192.168.1.8 \
dst-port=1900 protocol=udp src-address=192.168.88.0/24
add action=masquerade chain=srcnat dst-address=192.168.1.8 dst-port=443 \
protocol=tcp src-address=192.168.1.0/24
add action=masquerade chain=srcnat comment=88 dst-address=192.168.1.8 \
dst-port=443 protocol=tcp src-address=192.168.88.0/24
add action=masquerade chain=srcnat dst-address=192.168.1.7 dst-port=993 \
protocol=tcp src-address=192.168.1.0/24
add action=masquerade chain=srcnat dst-address=192.168.1.7 dst-port=587 \
protocol=tcp src-address=192.168.1.0/24
add action=masquerade chain=srcnat comment=88/24 dst-address=192.168.1.7 \
dst-port=587 protocol=tcp src-address=192.168.88.0/24
add action=masquerade chain=srcnat dst-address=192.168.1.7 dst-port=465 \
protocol=tcp src-address=192.168.1.0/24
add action=dst-nat chain=dstnat comment=DMZ disabled=yes in-interface=\
l2tp-out1 to-addresses=192.168.1.253
add action=dst-nat chain=dstnat comment="SIP -5060" dst-port=6060 \
in-interface=l2tp-out1 log-prefix=5060_ protocol=udp to-addresses=\
192.168.1.253 to-ports=5060
add action=dst-nat chain=dstnat comment="SIP -5061" dst-port=6061 \
in-interface=l2tp-out1 log-prefix=5061_ protocol=udp to-addresses=\
192.168.1.253 to-ports=5061
add action=dst-nat chain=dstnat comment="SIP -5160" dst-port=6160 \
in-interface=l2tp-out1 log-prefix=5160_ protocol=udp to-addresses=\
192.168.1.253 to-ports=5160
add action=dst-nat chain=dstnat comment="SIP -5160 - TEST" dst-port=5160 \
in-interface=l2tp-out1 log-prefix=5160_ protocol=udp to-addresses=\
192.168.1.253 to-ports=5160
add action=dst-nat chain=dstnat comment="SIP -5160 - LAN" dst-address=\
***.***.***.*** dst-port=5160 log-prefix=5160_ protocol=udp src-address=\
192.168.1.0/24 to-addresses=192.168.1.253 to-ports=5160
add action=dst-nat chain=dstnat comment="SIP -5160 - LAN-WIFI" dst-address=\
***.***.***.*** dst-port=5160 log-prefix=5160_ protocol=udp src-address=\
192.168.88.0/24 to-addresses=192.168.1.253 to-ports=5160
add action=dst-nat chain=dstnat comment="SIP -5161" dst-port=6161 \
in-interface=l2tp-out1 log-prefix=5161_ protocol=udp to-addresses=\
192.168.1.253 to-ports=5161
add action=dst-nat chain=dstnat comment="SIP -9000-10000" dst-port=\
10000-20000 in-interface=l2tp-out1 log-prefix=EEEE_ protocol=udp \
to-addresses=192.168.1.253 to-ports=10000-20000
add action=dst-nat chain=dstnat comment="RDP - .59" disabled=yes dst-port=\
17585 in-interface=l2tp-out1 protocol=tcp to-addresses=192.168.1.59 \
to-ports=3389
add action=dst-nat chain=dstnat comment=******* disabled=yes dst-port=****** \
in-interface=l2tp-out1 protocol=tcp to-addresses=192.168.1.150 to-ports=\
*****
/ip firewall service-port
set ftp disabled=yes
set tftp disabled=yes
set irc disabled=yes
set h323 disabled=yes
set sip disabled=yes ports=6060,6061
set pptp disabled=yes
set dccp disabled=yes
set sctp disabled=yes
/ip ipsec identity
add peer=peer1 remote-id=ignore secret=******
/ip route
add check-gateway=ping distance=2 gateway=***.***.***.***
add distance=1 dst-address=192.168.88.0/24 gateway=192.168.1.10
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set winbox address=192.168.1.0/24,192.168.3.0/24,192.168.88.0/24
set api-ssl disabled=yes
/ip ssh
set allow-none-crypto=yes forwarding-enabled=remote
/ip upnp
set enabled=yes
/ip upnp interfaces
add interface=bridge1 type=external
add interface=ether9 type=internal
/ppp secret
add name=vpn_ password=*************** profile=VPN-HOME service=l2tp
add name=honor_ password=*************** profile=VPN-HOME service=l2tp
add comment=******** local-address=192.168.3.13 name=********* \
password=***************** profile=VPN-HOME
/system clock
set time-zone-name=Europe/Moscow
/tool mac-server
set allowed-interface-list=none
/tool mac-server mac-winbox
set allowed-interface-list=none
/tool mac-server ping
set enabled=no
Сбрасывал кеш DNS - тоже никакого эффекта.
Еще смущает вот такая фигня в DNS после сброса кеша: Подскажите, пожалуйста, в чем моя ошибка?
Спасибо.