Весь трафик из дома шел через провайдера с оптикой, для быстрой и качественной работы сети интернет, а доступ извне в дом был через второго провайдера(мобильного, у которого осталась статика).
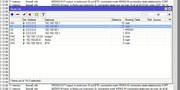
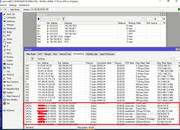
Казалось бы задача на 5 минут, но я не понимаю почему при маркировке соединения, при том что в логах Микротик пишет, что есть марка, он иногда отправляет через первого провайдера...
Первый провайдер подписан BTK, второй - KROKS.
Код: Выделить всё
# 2023-10-19 11:44:30 by RouterOS 7.10
# software id = WMIK-ATAJ
#
# model = RB962UiGS-5HacT2HnT
# serial number = 8A7708CE722B
/interface bridge
add arp=proxy-arp dhcp-snooping=yes igmp-snooping=yes name=bridge1
/interface ethernet
set [ find default-name=ether1 ] name=BTK
set [ find default-name=ether2 ] name=Kroks
/interface list
add name=WAN
add name=LAN
/ip pool
add name=dhcp_pool1 ranges=192.168.1.100-192.168.1.254
/ip dhcp-server
add address-pool=dhcp_pool1 interface=bridge1 lease-time=1d30m name=dhcp1
/routing table
add disabled=no fib name=BTK
add disabled=no fib name=KROKS
/interface bridge port
add bridge=bridge1 interface=ether3
add bridge=bridge1 interface=ether4
add bridge=bridge1 interface=ether5
/interface list member
add interface=BTK list=WAN
add interface=Kroks list=WAN
add interface=bridge1 list=LAN
/ip address
add address=192.168.1.1/24 interface=bridge1 network=192.168.1.0
add address=192.168.100.2/24 interface=BTK network=192.168.100.0
add address=192.168.88.2/24 interface=Kroks network=192.168.88.0
/ip dhcp-server network
add address=192.168.1.0/24 dns-server=192.168.1.1 gateway=192.168.1.1
/ip dns
set servers=8.8.8.8,8.8.4.4,1.1.1.1
/ip firewall filter
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related hw-offload=yes
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=accept chain=forward connection-state=\
established,related,untracked
add action=accept chain=input dst-port=8000,8001,554,555 protocol=tcp
add action=accept chain=input dst-port=8888,30464 protocol=tcp
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=forward protocol=icmp
add action=accept chain=input comment="accept all connection from LAN" \
in-interface-list=!WAN src-address=192.168.0.0/24
add action=accept chain=forward in-interface-list=!WAN out-interface-list=WAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=input dst-port=8291,22 protocol=tcp
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=accept chain=input dst-port=1723 protocol=tcp
add action=accept chain=input protocol=l2tp
add action=accept chain=input dst-port=1701,500,4500 protocol=udp
add action=accept chain=input protocol=gre
add action=accept chain=input protocol=ipsec-esp
add action=accept chain=input protocol=ipsec-ah
add action=accept chain=input comment="Allow DNS from LOCAL" dst-port=53 \
in-interface=bridge1 protocol=udp
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=WAN
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
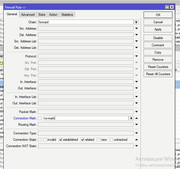
/ip firewall mangle
add action=mark-connection chain=input in-interface=BTK log=yes log-prefix=\
BTK-IN new-connection-mark=BTK-IN passthrough=yes
add action=mark-connection chain=input in-interface=Kroks log=yes log-prefix=\
KROKS-IN new-connection-mark=KRIKS-IN passthrough=yes
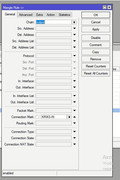
add action=mark-routing chain=output connection-mark=BTK-IN log=yes \
log-prefix=BTK-OUT new-routing-mark=BTK passthrough=yes
add action=mark-routing chain=output connection-mark=KRIKS-IN log=yes \
log-prefix=KROKS-OUT new-routing-mark=KROKS passthrough=yes
/ip firewall nat
add action=dst-nat chain=dstnat dst-port=8888,30464 in-interface-list=WAN \
log-prefix=ir protocol=tcp to-addresses=192.168.1.30
add action=dst-nat chain=dstnat dst-port=30464 protocol=tcp src-address=\
192.168.1.0/24 to-addresses=192.168.1.30
add action=masquerade chain=srcnat dst-address=192.168.1.30 dst-port=30464 \
protocol=tcp src-address=192.168.1.0/24
add action=dst-nat chain=dstnat dst-port=554 in-interface-list=WAN protocol=\
tcp to-addresses=192.168.1.201 to-ports=554
add action=dst-nat chain=dstnat dst-port=554 protocol=tcp src-address=\
192.168.1.0/24 to-addresses=192.168.1.201 to-ports=554
add action=masquerade chain=srcnat dst-address=192.168.1.201 dst-port=554 \
protocol=tcp src-address=192.168.1.0/24
add action=dst-nat chain=dstnat dst-port=8000 in-interface-list=WAN protocol=\
tcp to-addresses=192.168.1.201 to-ports=8000
add action=dst-nat chain=dstnat dst-port=8000 \
protocol=tcp src-address=192.168.1.0/24 to-addresses=192.168.1.201
add action=masquerade chain=srcnat dst-address=192.168.1.201 dst-port=8000 \
protocol=tcp src-address=192.168.1.0/24
add action=dst-nat chain=dstnat dst-port=555 in-interface-list=WAN protocol=\
tcp to-addresses=192.168.1.61 to-ports=554
add action=dst-nat chain=dstnat dst-port=555 protocol=tcp src-address=\
192.168.1.0/24 to-addresses=192.168.1.61 to-ports=554
add action=masquerade chain=srcnat dst-address=192.168.1.61 dst-port=554 \
protocol=tcp src-address=192.168.1.0/24
add action=dst-nat chain=dstnat dst-port=8001 in-interface-list=WAN protocol=\
tcp to-addresses=192.168.1.61 to-ports=8000
add action=dst-nat chain=dstnat dst-port=8001 \
protocol=tcp src-address=192.168.1.0/24 to-addresses=192.168.1.61 \
to-ports=8000
add action=masquerade chain=srcnat dst-address=192.168.1.61 dst-port=8000 \
protocol=tcp src-address=192.168.1.0/24
add action=masquerade chain=srcnat out-interface=Kroks
add action=masquerade chain=srcnat out-interface=BTK
/ip route
add disabled=no distance=10 dst-address=0.0.0.0/0 gateway=192.168.100.1 \
pref-src="" routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
add disabled=no distance=10 dst-address=0.0.0.0/0 gateway=192.168.88.1 \
pref-src="" routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
add disabled=no dst-address=0.0.0.0/0 gateway=192.168.88.1 routing-table=\
KROKS suppress-hw-offload=no
add disabled=no dst-address=0.0.0.0/0 gateway=192.168.100.1 routing-table=BTK \
suppress-hw-offload=no